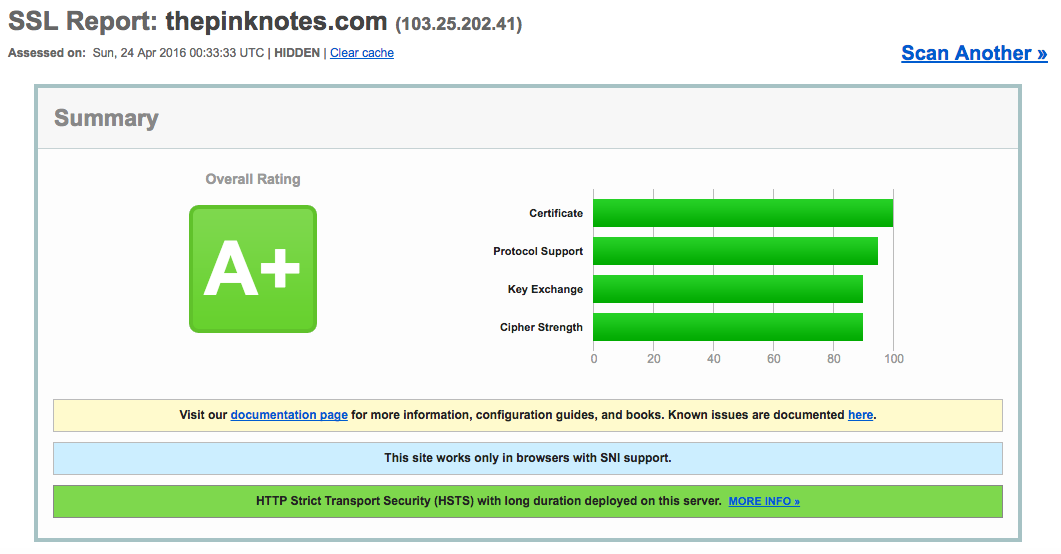
I tried running thepinknotes.com in Qualys SSL Labs SSL Server Test and found out that there were a couple of issues on my SSL configurations. I was only supposed to take a look but one thing led to another and decided to try and increase my score to A.
Here are the things that I changed in my configurations in order for me to accomplish that goal:
-
Corrected the SSL certificate order
I bought a COMODO certificate from namecheap.com a couple of months ago and tried to set it up. I didn’t realize that I concatenated the certificates wrongly (noob). To fix this, I recreated my certificate by concatenating it in the right order.
cat your_site_com.crt COMODORSADomainValidationSecureServerCA.crt COMODORSAAddTrustCA.crt AddTrustExternalCARoot.crt > final.crtI uploaded this new certificate in my server and restarted NGINX.
-
Enabling ssl-session-cache
This came up in the analysis report from ssl labs.
Session resumption (caching) No (IDs assigned but not accepted)This means that for every request a user makes, the SSL handshake will need to be re-established. This can be pretty costly. This can be reduced by caching the session.
To enable it, you simply need to add this in
/etc/nginx/nginx.conf:ssl_session_cache shared:ssl_session_cache:10m;This means that NGINX will share the session cache between workers. This will be stored for 10 minutes. For more information, you can check out this link.
For further reading:
-
Guarding against POODLE attack
POODLE attack exploits SSLv3 to reveal encrypted data. This is fairly easy to guard against. In NGINX, you need to add this line in
/etc/nginx/nginx.conf’shttpblock.ssl_protocols TLSv1 TLSv1.1 TLSv1.2;This will only enable the specified SSL protocols.
-
Strengthening the DH Key Exchange
I saw this comment in my analysis report:
This server supports weak Diffie-Hellman (DH) key exchange parameters.NGINX uses the default key given by OpenSSL as input to Diffie-Hellman Key Exchange.
This default key is using
1024numbits. To increase the strength of this key, I generated a new one using4096bits. If you don’t specifynumbitsit will default to2048bits.$ cd /etc/ssl/private/ $ openssl dhparam -out dhparam.pem 4096This will generate
dhparam.crtI used this new dhparam and configured it in NGINX by adding this in
/etc/nginx/nginx.conf’shttpblock.ssl_dhparam /etc/ssl/private/dhparams.pem -
HSTS
Because my website needs only to communicate in HTTPS, I have enabled HSTS.
To do this, I added this in the
serverblock for thepinknotes.com in my NGINX config.add_header Strict-Transport-Security max-age=15768000; -
Cipher configuration
I have also modified my cipher configuration for stricter rules in regards to the cipher used. I added this in
/etc/nginx/nginx.conf’shttpblock.ssl_ciphers "EECDH+AESGCM:EDH+AESGCM:ECDHE-RSA-AES128-GCM-SHA256:AES256+EECDH:DHE-RSA-AES128-GCM-SHA256:AES256+EDH:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES256-GCM-SHA384:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256:AES256-SHA:AES128-SHA:DES-CBC3-SHA:HIGH:!aNULL:!eNULL:!EXPORT:!DES:!MD5:!PSK:!RC4";I have also set the configuration to prefer using the server cipher over the client’s. To configure this, I have added this in the
httpblock.ssl_prefer_server_ciphers on;
After doing these changes, I managed to get an A+ on my SSL analysis. That’s been a fun Saturday fiddling about my SSL configuration and reading up on some of these concepts. The final outcome :-)
If you want to read more, I suggest you read this blog. It has more detailed information on some of the vulnerabilities.